Bearer Authorization
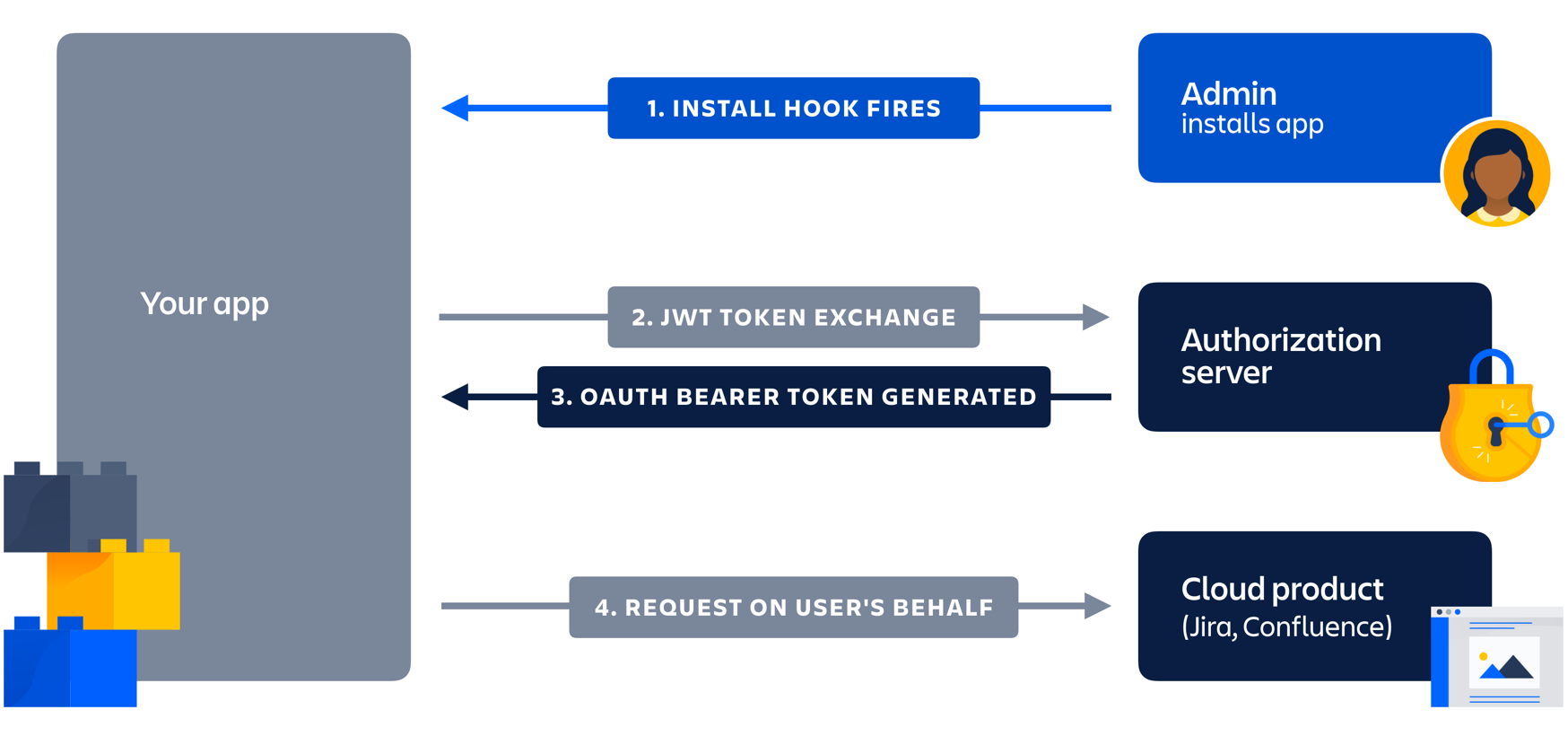
1. Write the following steps in the correct order:
1. Register your application to get a client_id and client_secret
2. Ask the client if they want to sign in via a third party
3. Make a request to a third-party API endpoint
4. Redirect to a third party authentication endpoint
5. Receive authorization code
6. Make a request to the access token endpoint
7. Receive access token
2. What can you do with an authorization code?
An authorization code is an alphanumeric password that authorizes its user to purchase, sell or transfer items, or to enter information into a security-protected space. An authorization code is typically a sequence of letters, numbers, or a combination of both, that validates a person’s identity, approves a transaction or provides access to a secured area.
The most common usage of authorization codes is those sent to a merchant from credit card issuers, to confirm that the customer’s credit card has sufficient credit available to authorize the transaction.
3. What can you do with an access token?
Access tokens are the thing that applications use to make API requests on behalf of a user. The access token represents the authorization of a specific application to access specific parts of a user’s data. Access tokens must be kept confidential in transit and in storage.
4. What’s a benefit of using OAuth instead of your own basic authentication?
It enables apps to obtain limited access (scopes) to a user’s data without giving away a user’s password. It decouples authentication from authorization and supports multiple use cases addressing different device capabilities. It supports server-to-server apps, browser-based apps, mobile/native apps, and consoles/TVs.
Terms:
Client ID: A client ID is a unique eight-digit number generated by the depository participants to easily identify their clients. This number is generated by using the in-house formula of your chosen brokerage house. It is not influenced in any way by the depositories. This client ID number is used to tie up all their services to the specific client. You can use this number to track your investment history.
Client Secret: A client secret is a secret known only to your application and the authorization server. It protects your resources by only granting tokens to authorized requestors.
Authentication Endpoint: Endpoint authentication is a security mechanism designed to ensure that only authorized devices can connect to a given network, site or service. The approach is also known as device authentication.
Access Token Endpoint: The token endpoint is where apps make a request to get an access token for a user. This section describes how to verify token requests and how to return the appropriate response and errors.
Authorization Code: An authorization code is typically a sequence of letters, numbers, or a combination of both, that validates a person’s identity, approves a transaction or provides access to a secured area.
Access Token: Access tokens are used in token-based authentication to allow an application to access an API. The application receives an access token after a user successfully authenticates and authorizes access, then passes the access token as a credential when it calls the target API. The passed token informs the API that the bearer of the token has been authorized to access the API and perform specific actions specified by the scope that was granted during authorization.